What is Vishing?
Vishing is a form of attack that attempts to trick victims into giving up sensitive personal information over the phone. While that makes it sound like an old-fashioned scam, vishing attacks have high-tech elements: they involve automated voice simulation technology, for instance, or the scammer may use personal information about the victim harvested from earlier cyberattacks to put them at ease.
No matter what technology is used, the setup for the attack follows a familiar social engineering script: An attacker creates a scenario to prey on human emotions, commonly greed or fear, and convinces the victim to disclose sensitive information, like credit card numbers or passwords. In that sense, vishing techniques mirror the phishing scams that have been around since the 1990s. But vishing calls exploit the fact that we’re more likely to trust a human voice — and may target the elderly and technophobic who are naive and have no experience with these types of scams.
What is Smishing and how it works.
Most smishing attacks work like email phishing. The attacker sends a message enticing the user to click a link or asks for a reply that contains the targeted user’s private data.
The information an attacker wants can be anything, including:
- Online account credentials.
- Private information that could be used in identity theft.
- Financial data that can be used to sell on darknet markets or for online fraud.
Smishers use a variety of ways to trick users into sending private information. They may use basic information about the target (such as name and address) from public online tools to fool the target into thinking the message is coming from a trusted source.
The smisher may use your name and location to address you directly. These details make the message more compelling. The message then displays a link pointing to an attacker-controlled server. The link may lead to a credential phishing site or malware designed to compromise the phone itself. The malware can then be used to snoop the user’s smartphone data or send sensitive data silently to an attacker-controlled server.
Social engineering is used in combination with smishing. The attacker might call the user asking for private information before sending a text message. The private information can then be used in the smisher’s text message attack. Several telecoms have tried to fight social engineering calls by displaying “Spam Risk” on a smartphone when a known scam number calls the user.
Malware is often stopped by basic Android and iOS security features. But even with robust security controls on mobile operating systems, no security controls can combat users who willingly send their data to an unknown number.
Example of a Smishing Attack
A more common smishing attack uses brand names with links purported to be to the brand’s site. Usually, an attacker will tell the user that they’ve won money or provide a malicious link purported to be for tracking packages, as in the following example.
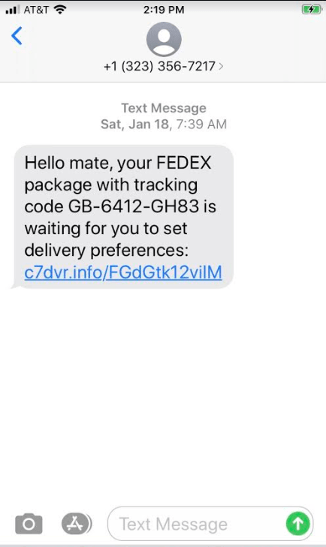
The language in the above message should be a warning sign for users familiar with the way smishing works. But many users trust SMS messages and aren’t thrown off by informal language.
Another warning sign is the URL: it does not point to an official FedEx URL. But not all users are familiar with official brand URLs and may ignore it.
Attackers use this type of message because someone is always waiting on a FedEx package. If the message is sent to thousands of recipients, it can trick many of them.
The link typically points to a site hosting malware or prompts the user to log in to their account. The authentication page is not on the official FedEx site, but it’s more difficult to see the full URL on a smartphone browser, and many users won’t bother checking.
How to Protect from Smishing Attacks
Like email phishing, protection from smishing depends on the targeted user’s ability to identify a smishing attack and ignore or report the message. If a phone number is often used in scams, the telecom might warn users who receive messages from a known scam number or drop the message altogether.
Smishing messages are dangerous only if the targeted user acts on it by clicking the link or sending the attacker private data.
Here are a few ways to detect smishing and to avoid becoming a victim:
- The message offers quick money either from winning prizes or collecting cash after entering information. Coupon code offerings are also popular.
- Financial institutions will never send a text asking for credentials or transfer of money. Do not ever send credit card numbers, ATM PINs, or banking information to someone in text messages.
- Avoid responding to a phone number that you don’t recognise.
- Messages received from a number with only a few digits probably came from an email address, which is a sign of spam.
- Banking information stored on the smartphone is a target for attackers. Avoid storing this information on a mobile device. Should an attacker install malware on the smartphone, this banking information could be compromised.
- Telecoms offer numbers to report attacks. To protect other users, send the message to your telecom’s number so that it can be investigated.
- Most phones now come with the ability to block spam numbers, it gives you the option to block that number.




